Software Security/Group 3/Code Scanning
We tried various tools to analyse the phpBB2 software. Each group member has a specific tool which he analysed in-depth.
Results
In this document we desribed our automated code scanning effort.
Fortify
360 v3.0.0 (Analyzers and Apps) was run on a Windows 7 64-bit machine. Since we ran into the 'insufficient memory'-problem as well, we ran Fortify on phpBB with the '-Xmx800M' parameter.
In Table 1 the scan results are shown. As one can see - when focussing on the error handler's security - the category System Information Leak is the only/most important category to audit. phpBB v2.0.0.0 contains at least 17 (perhaps not all leaks are found) of such system information leaks. All leaks are directly related to use of the three functions: error_reporting(), builtin_echo() and builtin_print().
Fortify specifies their description of a system information leak as follows:
An information leak occurs when system data or debugging information leaves the program through an output stream or logging function.
Then, Fortify gave very usefull details and recommendations. For example in the file upgrade.php at line 26 the information revealing by the function call to error_reporting() could help an adversary form a plan of attack. Furthermore an example is given:
The following code prints an exception to the standard error stream:
<?php
...
echo "Server error! Printing the backtrace";
debug_print_backtrace();
...
?>
Depending upon the system configuration, this information can be dumped to a console, written to a log file, or exposed to a remote user. In some cases the error message tells the attacker precisely what sort of an attack the system is vulnerable to. For example, a database error message can reveal that the application is vulnerable to a SQL injection attack. Other error messages can reveal more oblique clues about the system. In the example above, the search path could imply information about the type of operating system, the applications installed on the system, and the amount of care that the administrators have put into configuring the program.
Fortify's general recommendation for solving these kind of security holes are:
1. Do not rely on wrapper scripts, corporate IT policy, or quick-thinking system administrators to prevent system information leaks.
Write software that is secure on its own.
2. This category of vulnerability does not apply to all types of programs.
For example, if your application executes on a client machine where system information is already available to an attacker,
or if you print system information only to a trusted log file, you can use AuditGuide to filter out this category.
At first glance, Fortify seems to do a pretty good job in specifying, finding and listing several security holes. But then, the recommendations are quite poor. Fortify helps you with understanding the reported security hole, but does not give concrete solution, nor example solutions. Nevertheless, Fortify could helps a php-developer very/quite good in finding missed security holes.
| #Category | #Critical risks | #High risks | #Medium risks | #Low risks | #All risks |
|---|---|---|---|---|---|
| Cookie Security: HTTPOnly not set | 0 | 0 | 0 | 10 | 10 |
| Cookie Security: Persistent Cookie | 0 | 0 | 0 | 4 | 4 |
| CSS: Poor Validation | 0 | 0 | 1 | 2 | 3 |
| CSS: Reflected | 288 | 98 | 0 | 0 | 386 |
| Dangerous File Inclusion | 924 | 185 | 0 | 0 | |
| Dynamic Code Evaluation: Code Injection | 0 | 422 | 0 | 0 | 422 |
| Header Manipulation | 0 | 69 | 0 | 0 | 69 |
| Header Manipulation: Cookies | 0 | 484 | 0 | 0 | 484 |
| Insecure Randomness | 0 | 7 | 0 | 0 | 7 |
| Password Management: Empty Password | 0 | 12 | 0 | 0 | 12 |
| Password Management: Password in Comment | 0 | 0 | 0 | 10 | 10 |
| Path Manipulation | 23 | 611 | 0 | 0 | 634 |
| Privacy Violation | 0 | 24 | 0 | 0 | 23 |
| SQL Injection | 2248 | 337 | 0 | 0 | 2585 |
| System Information Leak | 0 | 0 | 0 | 17 | 17 |
| Weak Cryptographic Hash | 0 | 0 | 0 | 10 | 10 |
| TOTAL | 3483 | 2249 | 1 | 53 | 5786 |
Swaat
Swaat is not very easy to get running. We tried to run it in a Windows XP 3 vm with recent software. Unfortunately running Swaat on this configuration gives the following error:
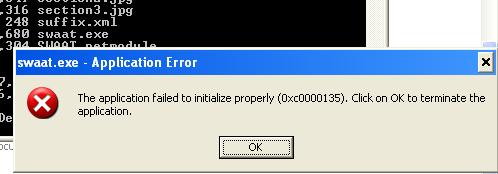
To fix this issue, one needs to uninstall recent Microsoft .NET frameworks and install an old version from the following url: .NET framework
Since PHP is still actively developed and Swaat (probably) not, we would not feel confident analyzing newer PHP code (PHP 5.x) with it. When it finally ran, it scanned the code quite quickly and found 14 high risks vulnerabilities, 2222 medium and 16 low.
Swaat raw results
Swaat generates a nice html report which can be found here
Results interpretation
Swaat classifies vulnerabilities in 3 categories. The program finds 14 occurrences of so called high vulnerabilities. In all these cases it concerns the eval function. The php.net site says the following about the eval function:
Evaluates the string given in code_str as PHP code. Among other things, this can be useful for storing code in a database text field for later execution.
There are some factors to keep in mind when using eval(). Remember that the string passed must be valid PHP code, including things like terminating statements with a semicolon so the parser doesn't die on the line after the eval(), and properly escaping things in code_str. To mix HTML output and PHP code you can use a closing PHP tag to leave PHP mode.
Also remember that variables given values under eval() will retain these values in the main script afterwards.
So it is important that this function never receives any 'user' input or otherwise unchecked input. A quick manual inspection of the source code shows that the code is checked and doesn't take user input (for the emailer.php case) so this warning might be a false positive. On the other side, the quick manual inspection only consists of looking up the supposedly bad code and taking a quick look at it to see if it is indeed wrong without analysing the entire context. Also, these warnings seem to be not very useful for our part, Error Handling and Logging, of the OWASP project. Some files indicated by swaat however, may include data that is eventually mailed to a user, so could be considered logging or error handling. In this case it is important that no confidential information is leaked.
Medium vulnerabilities
Swaat found 2222 medium classified vulnerabilities. Almost all of these are of the following form and rather vague:
There appears to be some text that may indicate security sensitive functionality. Ensure you track any variables or function calls here during manual source code review
This could be a handy start point for the manual analysis when considering error handling and logging, since it also indicates in which file the vulnerability occurs and the variables hint that this piece of code has to do with error messages:
In C:\Documents and Settings\Robbert\Desktop\swaat_source\phpBB2\admin\admin_users.php, line 601 (context is $error_msg .= ( ( isset($error_msg) ) ? '
' : ) . $lang['Admin_user_fail'];)
Others are more concrete but not relevant to our part of the project:
This parameter appears to be of a hidden type. Often developers believe that because hidden parameters are not viewable on the client's user interface they can't be changed by the client. This is not true, as users may employ proxies or manually specify parameters in the URL. Ensure that the parameter is not security sensitive (e.g. price, debug mode on or off, whether use is an admin or regular user,
Low vulnerabilities
All the low vulnerabilities are the same, Swaat gives the following explanation:
This function is subject to race conditions. This is typically because the resource might be modified between the time of check and time of use. This function does not always indicate a problem, but the code should be checked.
Looking at the code, this seems irrelevant for our part of the exercise.
Yasca
Yasca generates a cluttered html report which can be found here.
General comments: The running time for the checking was quite long. In my Ubuntu virtual machine it took 20 minutes. The HTML produced is good-looking, and it provides nice shortcuts to quickly see the line of code that is in error. It is too exhaustive though, with many false-positives, but this might be related to a) having an old version of phpBB and b) running bleeding-edge versions of the depended software.
Errors
Segmentation fault
I received a Segmentation fault on the output of my console. But I cannot see which plugin made this insolent mistake. This is once again a blunder on the part of yasca, for it should inform the user which test failed.
IntegrityCheck
Plugin IntegrityCheck is broken. It did work on the mockup data that is provided alongside with yasca. But it did not work when I targeted it at the phpBB code tree (see the .log file for details). Therefore I am inclined to believe it is a bug in the respective module, but I cannot rule out that my system configuration is of influence. Maybe a small code fix can help the problem. Nontheless, this plugin is at fault for breaking without proper error handling.
FxCop
Yasca is claimed to be cross platform, but plugin FxCop is in fact windows-only, and I did not use it. (It seems geared towards .NET code checking.)
Wikipedia says:
FxCop is a free static code analysis tool from Microsoft that checks .NET managed code assemblies for conformance to Microsoft's .NET Framework Design Guidelines. Unlike the lint programming tool for the C programming language, FxCop analyzes the compiled object code, not the original source code. It uses CIL parsing, and callgraph analysis to inspect assemblies for more than 200 different possible coding standards violations [...]
Thus, its relevance to phpBB seems quite zero.
PHP warning
When starting PHP with the provided Yasca script I get a warning that I haven't deciphered yet. But it seems ineffectual on the rest of the script.
[19-Apr-2011 08:54:19] PHP Warning: PHP Startup: Unable to load dynamic library '/usr/lib/php5/20090626+lfs/pdo.so' - /usr/lib/php5/20090626+lfs/pdo.so: cannot open shared object file: No such file or directory in Unknown on line 0
Clam AntiVirus
I got a warning that my version (the latest available on Ubuntu) is out of date. I disregarded this warning because the probability of finding a virus here is negligible.
'Yasca considered harmful'
One peculiar thing about Yasca is especially disheartening. Yasca itself does not correctly check input. It displays as summary "`.." (backtick is part of the quote) for the error of
`... && EXPR': found a value of type int - expected a boolean value
Apparently the double ampersands do not get properly handled.
Analysis
After running Yasca v2.2, we get 15326 hits. When looking at the Yasca results, we ignore the output from Rats since it is covered elsewhere. Rats results take up 35 hits.
PHPLint errors take up 6172 hits. It is inconceivable to determine whether any of this output is valid. Certainly most of it is not and are false positives. Skimming over the results, it becomes clear that due to PHPLint somehow misparsing, none of the hits can be properly evaluated. It is not even possible to guess which of the hits might be correct without doing a manual code review.
Two hits for weakness of credentials are given. They seem to come from Yasca internal detection mechanisms.
06208 | install.php:232 | $ftp_user = ( !empty($HTTP_POST_VARS['ftp_user']) ) ? $HTTP_POST_VARS['ftp_user'] ... 06209 | admin_users.php:71 | $username = ( !empty($HTTP_POST_VARS['username']) ) ? trim(strip_tags( $HTTP_POST_...
The description reads: Passwords that match the associated username are extremely weak and should never be used in a production environment, even if the password happens to meet the other rules for password complexity. The username should never match the password. This however is not the case here, hence a false positive.
PHPLint warnings take up 6763 hits. Again it is impossible to verify the results, for the same reason as above.
Next are 136 hits of using the count function inside for loops. This is claimed to be an inefficiency (I wonder though if the PHP interpreter does not optimize this automatically), but has no security relevance whatsoever.
Next are 3 Javascript-Lint errors. But they are quickly dismissed since they were generated on css files which are obviously without any Javascript.
Next are 74 informational warnings that simply grep-ed the file for the text strings of GPL, LGPL, etc. Useless clogging information.
Next are 266 informational messages that we should use ++$i instead of $i++. The speed gains are probably exaggerated and definitely not security related.
Then we again have the pleasure of finding 1510 PHPLint informational warnings which we cannot verify due to the aforementioned reasons.
Next we have 304 informational warnings that "file contents were changed" by IntegrityCheck plugin. 304 is still too much to verify manually. But we can speculate here that the tool merely checked for file changes, and not for harmful file changes. Therefore we can dismiss these results.
Finally we get 60 informational warnings that actually are correct. These messages complain that array indices should be quoted: Always quote array indexes. Use $foo['bar'] instead of $foo[bar]. This seems like a valid point, but it is hard to see how an attack can be made out of this.
Conclusion
As seen above, I found no correct positives in the Yasca output. But this was caused by the voluminous output of Yasca, which requires a complete manual code review to validate. In particular, PHPLint was accountable for 94% of the hits and is the most faulty Yasca plugin.
Pixy
While the tool would run without any problems, it failed to terminate on all but the smallest source files, producing no useful output. Though it looks promising, it is useless in its current state.
A code scan using Pixy could not be completed due to it taking too much resources. Results were obtained for some of the more trivial php files, but for these files only on of two warnings were obtained:
- Use of too many parameters in method calls, e.g.
Warning: More actual than formal params - call: /home/niels/2if06/project2/phpBB2/includes/functions.php:274 - callee: template<m> - decl: /home/niels/2if06/project2/phpBB2/includes/template.php:58
(Erik: This seems a rather worrying warning, doesn't it? Or do you have a clue why it might be harmless/explainable? My knowledge of PHP is too limited to explain why this construction is even valid, let alone why this would be useful. A short web search on the topic has been unsuccessful and therefore aborted.)
- Duplicate method definition, e.g.
Warning: Duplicate method definition due to include: sql_nextid<m> - found: /home/niels/2if06/project2/phpBB2/db/msaccess.php:351 - using: /home/niels/2if06/project2/phpBB2/db/mssql-odbc.php:349
The use of duplicate method definitions could introduce subtle vulnerabilities and it would be good practice to try and reduce the number of duplicates. Errors of this type in phpBB as found by Pixy occurred only in various source files defining the interface to various database systems. In this context using function overloading is correct technique as long as at most one database interface definition is loaded at any time. Still, this issue can be solved in a more robust way, for instance by defining different classes for each database interface which share common method names (or actually inherit from a base class if PHP supports this). Instances of these classes would also be a natural way of managing database connections.
Furthermore, Pixy claims it is able to detect vulnerabilities, however, none were found in the part of the code that was scanned. (Can you say something about which part of the code that was? Given that pixy finds no problems, the obvious question is whether this is (un)expected given the part of the code it looks at. This is the result of analysis of config.php, the only file for which Pixy managed to produce a full report. The lack of output is not surprising, since this file is empty.) Sample output is shown below
*** detecting vulnerabilities *** ***************** XSS Analysis BEGIN ***************** Number of sinks: 0 XSS Analysis Output -------------------- Total Vuln Count: 0 ***************** XSS Analysis END ***************** ***************** SQL Analysis BEGIN ***************** Number of sinks: 0 SQL Analysis Output -------------------- Total Vuln Count: 0 ***************** SQL Analysis END ***************** Total Time: 0 seconds
Rats
Command: rats.exe -w 3 --xml C:\phpBB2 >> output.xml
<severity>High</severity> <type>gzopen</type> <message> Argument 1 to this function call should be checked to ensure that it does not come from an untrusted source without first verifying that it contains nothing dangerous. </message> <file> <name>C:\phpBB2/admin/admin_db_utilities.php</name> <line>937</line> </file>
<severity>High</severity> <type>fopen</type> <message> Argument 1 to this function call should be checked to ensure that it does not come from an untrusted source without first verifying that it contains nothing dangerous. </message> <file> <name>C:\phpBB2/admin/admin_db_utilities.php</name> <line>952</line> </file> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>739</line> </file> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>408</line> </file> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>144</line> <line>183</line> </file> <file> <name>C:\phpBB2/includes/bbcode.php</name> <line>47</line> </file> <file> <name>C:\phpBB2/includes/emailer.php</name> <line>124</line> <line>239</line> <line>316</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>141</line> </file> <file> <name>C:\phpBB2/install.php</name> <line>467</line> <line>716</line> <line>747</line> <line>920</line> </file>
<severity>High</severity> <type>eval</type> <message> Argument 1 to this function call should be checked to ensure that it does not come from an untrusted source without first verifying that it contains nothing dangerous. </message> <file> <name>C:\phpBB2/contrib/template_db_cache.php</name> <line>158</line> <line>201</line> <line>224</line> <line>233</line> </file> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>151</line> <line>193</line> <line>219</line> <line>228</line> </file> <file> <name>C:\phpBB2/includes/bbcode.php</name> <line>61</line> </file> <file> <name>C:\phpBB2/includes/template.php</name> <line>127</line> <line>151</line> <line>174</line> <line>183</line> </file>
<severity>High</severity>
<type>mail</type>
<message>
Arguments 1, 2, 4 and 5 of this function may be passed to an external
program. (Usually sendmail). Under Windows, they will be passed to a
remote email server. If these values are derived from user input, make
sure they are properly formatted and contain no unexpected characters or
extra data.
</message>
<file>
<name>C:\phpBB2/includes/emailer.php</name>
<line>216</line>
</file>
<severity>Medium</severity> <type>fsockopen</type> <message> Argument 1 to this function call should be checked to ensure that it does not come from an untrusted source without first verifying that it contains nothing dangerous. </message> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>360</line> </file> <file> <name>C:\phpBB2/includes/smtp.php</name> <line>126</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>106</line> </file>
<severity>Medium</severity> <type>is_link</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. The following line(s) contain uses that may match up with this check: 726 (opendir) </message> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>724</line> </file>
<severity>Medium</severity> <type>is_link</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. The following line(s) contain uses that may match up with this check: 248 (opendir) </message> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>246</line> </file>
<severity>Medium</severity> <type>is_readable</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. The following line(s) contain uses that may match up with this check: 316 (fopen) </message> <file> <name>C:\phpBB2/includes/emailer.php</name> <line>314</line> </file>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/admin/admin_board.php</name> <line>18</line> </file> <file> <name>C:\phpBB2/admin/admin_db_utilities.php</name> <line>35</line> </file> <file> <name>C:\phpBB2/admin/admin_disallow.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_forumauth.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_forums.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_forum_prune.php</name> <line>26</line> </file> <file> <name>C:\phpBB2/admin/admin_groups.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_mass_email.php</name> <line>26</line> </file> <file> <name>C:\phpBB2/admin/admin_ranks.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_smilies.php</name> <line>33</line> </file> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_ug_auth.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_user_ban.php</name> <line>27</line> </file> <file> <name>C:\phpBB2/admin/admin_words.php</name> <line>27</line> </file>
<vulnerability>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> C:\phpBB2/admin/admin_db_utilities.php </file>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/admin/admin_db_utilities.php</name> <line>952</line> </file> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>739</line> </file> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>408</line> </file> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>144</line> <line>183</line> </file> <file> <name>C:\phpBB2/includes/bbcode.php</name> <line>47</line> </file> <file> <name>C:\phpBB2/includes/emailer.php</name> <line>124</line> <line>239</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>141</line> </file> <file> <name>C:\phpBB2/install.php</name> <line>467</line> <line>716</line> <line>747</line> <line>920</line> </file>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/admin/admin_smilies.php</name> <line>71</line> </file> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>131</line> <line>547</line> <line>787</line> </file> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>719</line> </file> <file> <name>C:\phpBB2/admin/index.php</name> <line>56</line> <line>171</line> </file> <file> <name>C:\phpBB2/includes/functions_selects.php</name> <line>31</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>241</line> </file>
<severity>Low</severity> <type>is_dir</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/admin/admin_smilies.php</name> <line>75</line> </file>
<severity>Low</severity> <type>is_dir</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/contrib/template_db_cache.php</name> <line>80</line> </file>
<severity>Low</severity> <type>is_dir</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>80</line> </file>
<severity>Low</severity> <type>is_dir</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/includes/template.php</name> <line>77</line> </file>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/admin/admin_smilies.php</name> <line>136</line> </file> <file> <name>C:\phpBB2/contrib/template_db_cache.php</name> <line>315</line> </file> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>317</line> </file> <file> <name>C:\phpBB2/includes/functions_search.php</name> <line>114</line> <line>115</line> </file> <file> <name>C:\phpBB2/includes/template.php</name> <line>265</line> </file> <file> <name>C:\phpBB2/search.php</name> <line>238</line> <line>239</line> </file> <file> <name>C:\phpBB2/upgrade.php</name> <line>197</line> <line>283</line> </file>
<severity>Low</severity> <type>is_link</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>135</line> </file>
<severity>Low</severity> <type>is_link</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>792</line> </file>
<severity>Low</severity> <type>is_file</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/admin/admin_styles.php</name> <line>552</line> </file>
<severity>Low</severity> <type>is_file</type> <message> A potential TOCTOU (Time Of Check, Time Of Use) vulnerability exists. This is the first line where a check has occured. No matching uses were detected. </message> <file> <name>C:\phpBB2/includes/functions_selects.php</name> <line>36</line> </file>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/admin/admin_users.php</name> <line>249</line> <line>317</line> <line>426</line> <line>430</line> <line>447</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>58</line> <line>147</line> <line>193</line> <line>200</line> </file> <file> <name>C:\phpBB2/install.php</name> <line>465</line> <line>482</line> </file>
</vulnerability> <vulnerability>
<severity>Low</severity> <type>fixed size local buffer</type> <message> A potential race condition vulnerability exists here. Normally a call to this function is vulnerable only when a match check precedes it. No check was detected, however one could still exist that could not be detected. </message> <file> <name>C:\phpBB2/contrib/template_file_cache.php</name> <line>149</line> <line>188</line> </file> <file> <name>C:\phpBB2/includes/usercp_avatar.php</name> <line>221</line> </file>
Own approach
Jeroen has written his own perl implementation to detect and catagorize error handling attempts in the code. It can be found here. The php manual offers a lot of different functions for error handling. Some more usefull or secure then others. To find all functions we had to search trough all the files. This is wat the script does, it takes an array with the specified functions (see list below) and count how many times they appear in a file. The script try's all .php and .inc files in a given directory. It also recurses on it. When it is finished it writes a table with the file name succedeed by the nummer of apperance of the given function.
- 1 File
- 2 debug_backtrace
- 3 debug_print_backtrace
- 4 error_get_last
- 5 error_log
- 6 error_reporting
- 7 restore_error_handler
- 8 restore_exception_handler
- 9 set_error_handler
- 10 set_exception_handler
- 11 trigger_error
- 12 user_error
- 13 die
phpbb/groupcp.php 0 0 0 0 0 0 0 0 0 0 0 40
phpbb/faq.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/search.php 0 0 0 0 0 0 0 0 0 0 0 16
phpbb/common.php 0 0 0 0 1 0 0 0 0 0 0 3
phpbb/posting.php 0 0 0 0 0 0 0 0 0 0 0 20
phpbb/includes/topic_review.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/includes/usercp_activate.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/includes/usercp_register.php 0 0 0 0 0 0 0 0 0 0 0 13
phpbb/includes/constants.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/includes/prune.php 0 0 0 0 0 0 0 0 0 0 0 9
phpbb/includes/functions_selects.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/includes/bbcode.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/includes/functions_post.php 0 0 0 0 0 0 0 0 0 0 0 29
phpbb/includes/usercp_viewprofile.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/includes/usercp_email.php 0 0 0 0 0 0 0 0 0 0 0 7
phpbb/includes/emailer.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/includes/smtp.php 0 0 0 0 0 0 0 0 0 0 0 7
phpbb/includes/functions.php 0 0 0 0 0 0 0 0 0 0 0 9
phpbb/includes/auth.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/includes/page_header.php 0 0 0 0 0 0 0 0 0 0 0 5
phpbb/includes/sql_parse.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/includes/template.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/includes/db.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/includes/page_tail.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/includes/usercp_avatar.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/includes/sessions.php 0 0 0 0 0 0 0 0 0 0 0 11
phpbb/includes/functions_validate.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/includes/functions_admin.php 0 0 0 0 0 0 0 0 0 0 0 8
phpbb/includes/usercp_sendpasswd.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/includes/functions_search.php 0 0 0 0 0 0 0 0 0 0 0 12
phpbb/update_to_FINAL.php 0 0 0 0 0 0 0 0 0 0 0 12
phpbb/memberlist.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/install.php 0 0 0 0 1 0 0 0 0 0 0 0
phpbb/viewtopic.php 0 0 0 0 0 0 0 0 0 0 0 22
phpbb/upgrade.php 0 0 0 0 1 0 0 0 0 0 0 0
phpbb/contrib/template_file_cache.php 0 0 0 0 0 0 0 0 0 0 0 6
phpbb/contrib/template_db_cache.php 0 0 0 0 0 0 0 0 0 0 0 8
phpbb/admin/admin_users.php 0 0 0 0 0 0 0 0 0 0 0 16
phpbb/admin/admin_forumauth.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/admin/page_footer_admin.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/admin/admin_disallow.php 0 0 0 0 0 0 0 0 0 0 0 5
phpbb/admin/admin_ranks.php 0 0 0 0 0 0 0 0 0 0 0 11
phpbb/admin/pagestart.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/admin/admin_forum_prune.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/admin/admin_db_utilities.php 0 0 0 0 0 0 0 0 0 0 0 12
phpbb/admin/admin_mass_email.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/admin/page_header_admin.php 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/admin/admin_styles.php 0 0 0 0 0 0 0 0 0 0 0 24
phpbb/admin/admin_forums.php 0 0 0 0 0 0 0 0 0 0 0 48
phpbb/admin/admin_board.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/admin/admin_user_ban.php 0 0 0 0 0 0 0 0 0 0 0 10
phpbb/admin/admin_groups.php 0 0 0 0 0 0 0 0 0 0 0 21
phpbb/admin/admin_ug_auth.php 0 0 0 0 0 0 0 0 0 0 0 21
phpbb/admin/admin_smilies.php 0 0 0 0 0 0 0 0 0 0 0 15
phpbb/admin/index.php 0 0 0 0 0 0 0 0 0 0 0 3
phpbb/admin/admin_words.php 0 0 0 0 0 0 0 0 0 0 0 9
phpbb/config.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/modcp.php 0 0 0 0 0 0 0 0 0 0 0 37
phpbb/profile.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/viewonline.php 0 0 0 0 0 0 0 0 0 0 0 2
phpbb/viewforum.php 0 0 0 0 0 0 0 0 0 0 0 11
phpbb/login.php 0 0 0 0 0 0 0 0 0 0 0 4
phpbb/db/mysql.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/oracle.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/mysql4.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/msaccess.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/mssql.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/postgres7.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/db2.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/db/mssql-odbc.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/index.php 0 0 0 0 0 0 0 0 0 0 0 8
phpbb/language/lang_english/lang_main.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/language/lang_english/lang_bbcode.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/language/lang_english/lang_admin.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/language/lang_english/lang_faq.php 0 0 0 0 0 0 0 0 0 0 0 0
phpbb/extension.inc 0 0 0 0 0 0 0 0 0 0 0 1
phpbb/privmsg.php 0 0 0 0 0 0 0 0 0 0 0 40