Software Security/Group 2/Code Scanning/CodeSecure
After running CodeSecure (with a license) on the phpBB2 web application the tool reported about 2500 different possible vulnerabilities. Most of these vulnerabilities are not important to us however, since we are only focusing on Output Encoding/Escaping for SQL.
We will not go into detail about the pros and cons of the tool. For a detailed review of the tool please head over to the evaluation page.
Below are the results of the 41-hour-scan we ran on a laptop using CodeSecure 4.2.0. This page is divided into three sections: a summary of the findings of the scan followed by the settings used in running the scan, and the last part lists the number of vulnerabilities CodeSecure found in each category it distinguishes.
Inhoud
- 1 Scan Summary
- 2 Scan Settings
- 3 Vulnerability Specification
- 4 CodeSecure SQL analysis
- 4.1 page 10-11 XSS Tainted Database
- 4.2 page 31-32 CRLF Injection, email address from tainted database
- 4.3 page 34 Email address from tainted database
- 4.4 page 37-38 Resource injection with data with data from tainted database
- 4.5 page 39 Resource injection tainted database
- 4.6 page 42 Cross side scripting (tainted database)
- 4.7 page 47-50 File inclusion with data from tainted database
- 4.8 page 52-53 File inclusion (tainted database)
- 4.9 page 57-58 File inclusion (tainted database)
- 4.10 page 60-61 File inclusion (tainted database)
- 4.11 page 80 HTTP Response Splitting (tainted database)
- 4.12 page p92-98 Cross side scripting (tainted database)
Scan Summary
| Duration | Did not complete |
| Scanned Files | 101 |
| Scanned Lines | 43,130 |
| Entry Points | 62 |
| Vulnerable Entry Points | 24 |
| Resulting Vulnerabilities | 2,571 |
| Vulnerable Statements | 53 |
| Vulnerable Files | 16 |
| Path | Filename | Vuln# | Warnings |
|---|---|---|---|
| /phpBB2/ | install.php | 470 | 4 |
| /phpBB2/ | groupcp.php | 296 | 0 |
| /phpBB2/ | modcp.php | 286 | 0 |
| /phpBB2/admin/ | admin_forums.php | 253 | 0 |
| /phpBB2/admin/ | admin_styles.php | 128 | 2 |
Scan Settings
Most of the following data comes directly from the report CodeSecure generated after running the scan.
| Scan Type | immediate |
| Policy Name | Default Policy |
| Tainted Source Type(s) | Web Request,Property Configuration,XML,File,Network Input,Web Service,Database,Command Line Arguments,Private,Hard-coded Value,System Environment,Exception Handling,Console,Window Form,Session,Pattern,None |
| Vulnerability Modules | Cross-Site Scripting|HTTP Response Splitting|XPath Injection|Resource Injection|File Inclusion|SQL Injection|Blind SQL Injection|Command Injection|Hard-Coded Password|Struts Validator Config|API Abuse|Information|Leak of System Data|LDAP Injection|Open Redirect|Tag Injection|CRLF Injection|Code Injection|Risky Cryptographic Algorithm|Insecure Randomness|Log Forging|Obsolete Functions|Session Variable Poisoning|Information Leak Through Log Files |
| Traceback Setting | One most vulnerable traceback |
| Merge Unknown | No |
| CPU | Intel Core i5 460M |
| RAM | 4 GB |
| HDD | 500 GB |
Vulnerability Specification
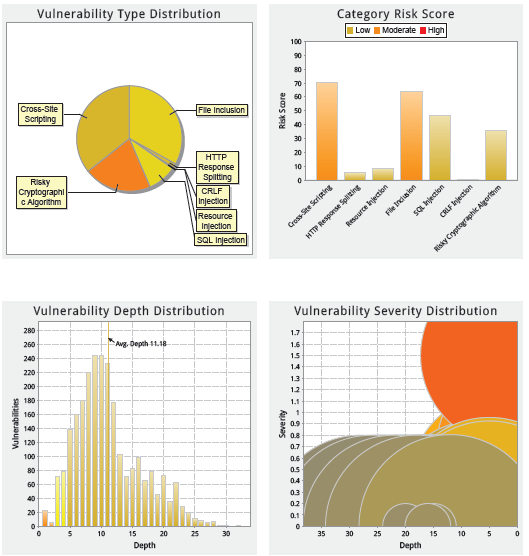
| Vulnerability Type | Vulnerable Statement | Resulting Vulnerability |
|---|---|---|
| CRLF Injection | 1 | 5 |
| Resource Injection | 2 | 4 |
| File Inclusion | 8 | 849 |
| HTTP Response Splitting | 18 | 33 |
| SQL Injection | 1 | 229 |
| Risky Cryptographic Algorithm | 5 | 534 |
| Cross-Site Scripting | 18 | 917 |
With the above table go the following charts, all of which are taken from CodeSecure's report as well.
CodeSecure SQL analysis
Below we will give a short description of the relevant vulnerabilities found by CodeSecure
page 10-11 XSS Tainted Database
Constant CONFIG_TABLE gets defined by previously taitned variable $table_prefix. This constant is used in an SQL query ("SELECT * FROM ". CONFIG_TABLE). Data from this query is added to a string that is output to the page.
page 31-32 CRLF Injection, email address from tainted database
SQL contains previously tainted $group_id variable and is executed. Field from database set as email address in email interpreter.
page 34 Email address from tainted database
SQL contains previously tainted $group_id variable and is executed. Field from database set as email address in email interpreter.
page 37-38 Resource injection with data with data from tainted database
SQL contains previously tainted $group_id variable and is executed. Field from database is used in variable declaration. This variable is used in fopen statement.
page 39 Resource injection tainted database
Field from tainted database is used in fopen statement.
page 42 Cross side scripting (tainted database)
Tainted database data is output to HTML
page 47-50 File inclusion with data from tainted database
Data from tainted is used in variable $template_name, this variable is used in include statement.
page 52-53 File inclusion (tainted database)
page 57-58 File inclusion (tainted database)
page 60-61 File inclusion (tainted database)
page 80 HTTP Response Splitting (tainted database)
Header location is changed with data from tainted database
page p92-98 Cross side scripting (tainted database)
Data from sql database is output to HTML