Security in Organizations/het werk/werkstuk/2012-13/Groep Ahmed en Edwin
Inhoud
Introducton[1]
The faculty consists of research and education institutes and various service departments. The dean and two vice-deans are in charge. They are being advised by a student-assessor. Together they are the Faculty Board.
The Faculty Assembly is the meeting in which the dean, Onderdeelcommissie (representing the faculty personnel) and the Student Board participate. The dean needs the permission of Faculty Assembly for every decision to change or finalize the faculty regulations, educational- and exam-regulations, the way of quality-control and policy-plans. The Faculty Assembly gives advice about reorganizations of the faculty and the appointment of professors.
Management approval
Representatives of the following committees should be participating in the approval of the security policy:
- Faculty Board;
- Onderdeelcommissie (representing the faculty personnel);
- Student Board;
- ICT;
- Property management;
- Fire brigade;
- Police.
Definition of information security[2][3]
Information security is about regulating access to assets. To clarify, the underlined words will be explained in more detail below:
- Regulating access consists from identification, authentication and authorisation.
- Assets are data that need protection.
In other words, information security protects assets from unauthorized access or modification in order to ensure availability, confidentiality and integrity.

Core processes of Faculty of Science:
- educating students to scientists;
- conducting scientific research.
In order to ensure that these processes run safely, a properly functioning information security platform needs to be present.
Basic principles to follow
Regarding to information security, the following issues have to be taken into account by the Faculty of Science:
- sensitive information in regards to personal privacy (name, address, salary, grades etc.) of staff members and students has to be well protected;
- systems like Blackboard and Osiris have to be safe-guarded and monitored to prevent unauthorized activities to occur;
- competitively sensitive information has to be well protected;
- research information needs to be protected properly;
- faculty computers which are being used by staff and students, need to have the necessary security equipment (both physically and digitally) to make sure they are properly protected;
- there should be a restriction on access to certain parts of the faculty (think of spaces where dangerous substances or confidential information are being kept);
- finally, the faculty (wireless) network environment must be well monitored to ensure safety.
Protecting the above listed issues is necessary to ensure confidentiality and integrity of the mentioned data.
Objective and scope
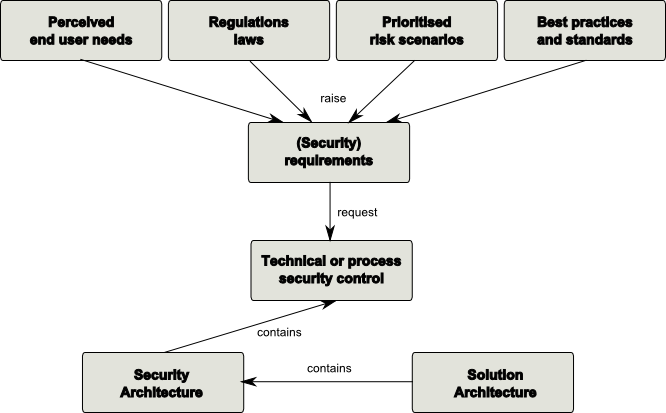
Requirements[4]
The main goal of the IT requirements is to ensure that the system maintains the confidentiality and integrity of all data that is classified as confidential and integer. Both the IT and physical security requirements are addressed in the chapters beneath. For a good overview, the requirements are divided into three parts.
Functional Security Requirements
- Authentication method(s) need(s) to be present;
- authorization check needs to be preformed in order to protect information/data;
- back-up of the concerning data needs to be performed on specific moments consequently;
- server clustering is necessary (e.g. to make sure server failure is not fatal to the concerning data).
Non-Functional Security Requirements
- Robustness Is very important in regards to both digital robustness (e.g. must withstand malicious activities) and physical robustness (e.g. hardware needs to be of acceptable quality such that it can withstand overheating) ;
- minimal performance must be set in advance in order to ensure a secure environment for the stakeholders to work in;
- the necessary measurements need to be taken to ensure security scalability if deeded.
Secure Development Requirements
- Data (digital or raw) needs to be classified properly;
- coding guidelines need to be present and protected;
- there has to be a predefined testing methodology to ensure that security is at desirable level;
- the concerning tests need to be performed at certain predefined moments consequently.
Policy scope[5]
The security policies within the concerning scope are all the policies that are needed to cover all information and data that need protection within the faculty.
Think of:
- data stored on the faculty databases;
- data stored on computers that belong to the faculty (also think of laptops given to staff by the faculty);
- transmitted across and public networks;
- printed or handwritten on paper, white boards etc.;
- sent by fax, telex or other communication methods;
- stored on removable media such as CD-ROMs, external hard disks, USB-sticks and other types of media;
- stored on fixed media such as hard disks and disk sub-systems;
- held on film or microfiche;
- presented on slides and overhead projectors using visual and audio media;
- spoken during telephone/VoIP calls and meetings or conveyed by any other method.
Organization of information security
Roles and responsibilities[6]
Security roles and responsibilities of employees, contractors and third party users are:
| Roles | Responsibility | ||||
|---|---|---|---|---|---|
| Faculty Board |
| ||||
| 'Onderdeelcommissie'
(representative of the faculty staff) |
| ||||
| Student Board |
| ||||
| Property management |
| ||||
| ICT |
| ||||
| Police |
| ||||
| Fire brigade |
| ||||
Roles of management, employees and students
The role of the management is enabling the security protocol. Their main responsibility in regard to this subject is to ensure that the right parties cooperate and they are also responsible for the relevant budget. Consequently the management is ultimately responsible for the extent to which a security protocol can be established. It is important that they retain an overall view of the entire security process.
The employees will play an active part in drafting the security protocol. This is because the staff in general has the most insight into their own working environment. Since this protocol is applicable to a scientific institute, the employees are eventually the ones who will benefit from an appropriate level of security that will be established in their working environment. This is because a researcher will not benefit if results of his/her research are prematurely compromised or lost. Both the employee and management will also have to determine what the repercussions are in case the security protocol is broken. This is because for example for a researcher it is not beneficial when research results are prematurely compromised or lost. Both the employees and management have to determine what the repercussions are in case the security protocol is broken.
Students will only be able to advise where and how the security protocol can be improved. All individuals who are somehow affiliated to the university will be informed of the security protocol. This varies by individual. This is because e.g. a facility employee generally does not not needed to deal with computers. However, every employee is obliged to follow the security protocol.
Approach [7][8][9][10][11][12][13]
For the faculty of science as well as for every other organisation, inventorying information systems is crucial for several reasons. By inventorying information systems, the faculty is able to determine which systems there are, where they are localized, what they do and who the system owner is.
Beneath an example is given of a two way approach:
1. using a concise table in which all systems are included. The table consists from the system number en system name. Also, a description needs to be added in order to explain what the concerning systems functionalities are. Then a system owner needs to be assigned to the concerning system. The main responsibility of the system owner is to manage user access and user rights in regards to authorisation. The picture below is an example of a concise system inventory.
| # | System name | System function | System owner |
|---|---|---|---|
| xxxxx | Osiris | Osiris-functionality: 1. providing students information about their grades, academic progress, registration of courses and exams, etc.; |
xx xx |
| xxxxx | Student mail | Central e-mail service for students | xx xx |
| xxxxx | Blackboard | Electronic learning environment for students by providing education (through courses) via the Internet and provide information to selected audiences through portal pages and organization pages. | xx xx |
| xxxxx | etc. | etc. | xx xx |
| xxxxx | |||
| xxxxx |
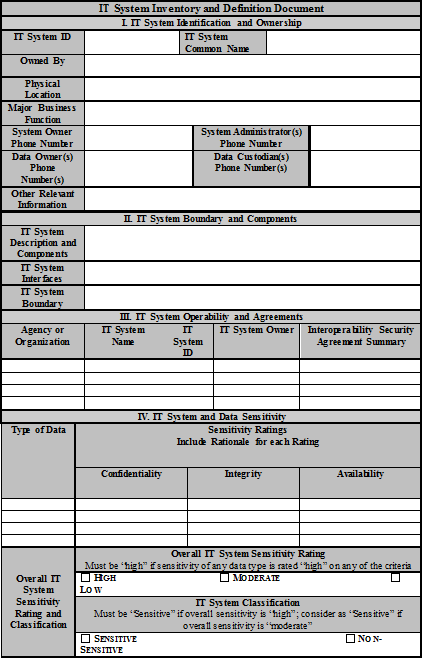
2. moreover, for every system, detailed information needs to be present if necessary. This concerns information which describes a system explicitly. The picture below is an example of an extended inventory of the system.[6]
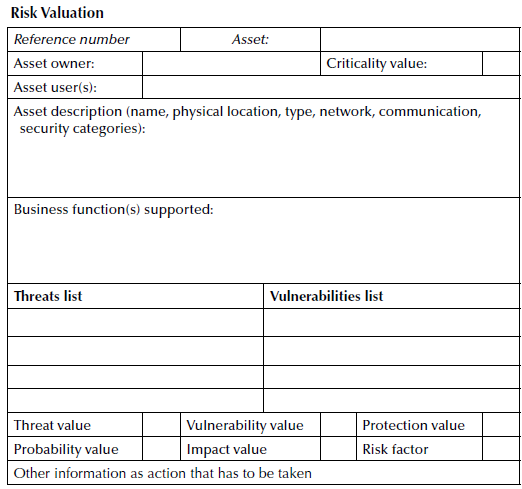
Risk valuation
To ensure that risks are being assessed properly, prerisk assessment (table below) needs to be performed regularly to ensure a proper risk valuation. Risk valuation is a collective recording of asset information, business functions the asset supports, vulnerabilities, threats, and relevant valuations. Each asset receives a valuation for threat, probability of threat occurrence, vulnerability level, protection, probability, impact, and risk factor.[6]
The risk assessors can focus on the vulnerabilities of key assets. Vulnerability classifications include technical (e.g., software, hardware, electric), natural phenomenon (e.g., hurricane, flood), external events (e.g., major application vendor goes out of business), and personnel (e.g., key knowledge with only one person and unrecorded).
Finely, these risks need to be tackled. In some parts of the ISO/IEC 27000-series is described that for an organization there are four options available to deal with risks in general:
- reducing the risk by implementing controls;
- avoiding the risk;
- transferring the risk;
- accepting the risk.
Needless to say, tackling these risks will happen in a different phase (certainly not in the Plan phase).
The best way for the faculty of science to improve the inventory of the systems consists of three parts:
- the current inventory needs to be checked;
- an approach needs to be developed for possible improvements;
- objectives need to be determined for these improvements.
Do, Check, Act
How to ensure that:
- additional controls are implemented (Do);
- information security is reviewed (Check);
- management review of information security is performed (Act).
As already mentioned an inventory of all physical systems and spaces within the faculty must be created by buildingmanagement and systemsmanagement. Anyone who is directly involved with the faculty - e.g. students, facility services, professors etc.. - will be asked to indicate which systems they use, who is the owner thereof and the risks to which these systems are vulnerable to. Also, with the request an announced will be made that within a, yet to be determined, period for those systems where no reaction has occurred, all access is closed. For these, the so-called, chirp system will enter into force. Of all owners it is expected to start drafting a security protocol for their own system. This can obviously be support by either external or internal experts. Owners who fail in this will be urged, a yet to be determined number of times, to start drafting their security protocol. Remains the owner in default his given access to the system will be revoked. Initially the security protocols may be reviewd by either internal or external security experts. There on the faculty a number of courses regarding security are included, the periodic review of the security protocol cann be imbedded as part of these security-related courses. It follows that to the management it will be proven that regular calibration takes place.
Baselines[9][14]
| # | Section # | Topic | Control | Cost | Effectiveness |
|---|---|---|---|---|---|
| 1 | 5.1.1 | Information security policy document | An information security policy document should be approved by management, and published and communicated to all employees and relevant external parties. | €1000,00 | 556 |
| 2 | 5.1.2 | Review of the information security policy | € 200,00 | 210 | |
| 3 | 6.1.1 | Management commitment to information security | € 750,00 | 135 | |
| 4 | 6.1.2 | Information security coordination | € 500,00 | 120 | |
| 5 | 6.1.3 | Allocation of information security responsibilities | € 300,00 | 205 | |
| 6 | 8.1.1 | Roles and responsibilities | Security roles and responsibilities of employees, contractors and third party users should be defined and documented in accordance with the organizations information security policy. | € 400,00 | 285 |
| 7 | 8.2.1 | Management responsibilities | Management should require employees, contractors and third party users to apply security in accordance with established policies and procedures of the organization. | € 400,00 | 150 |
| 8 | 8.3.3 | Removal of access rights | The access rights of all employees, contractors and third party users to information and information processing facilities should be removed upon termination of their employment, contract or agreement, or adjusted upon change. | € 200,00 | 365 |
| 9 | 10.1.2 | Change management | Changes to information processing facilities and systems should be controlled. | €1000,00 | 476 |
| 10 | 10.1.3 | Segregation of duties | Duties and areas of responsibility should be segregated to reduce opportunities for unauthorized or unintentional modification or misuse of the organizations assets. | € 300,00 | 375 |
| 11 | 10.4.1 | Controls against malicious code | Detection, prevention, and recovery controls to protect against malicious code and appropriate user awareness procedures should be implemented. | € 600,00 | 440 |
| 12 | 10.4.2 | Controls against mobile code | Where the use of mobile code is authorized, the configuration should ensure that the authorised mobile code operates according to a clearly defined security policy, and unauthorized mobile code should be prevented from executing. | € 600,00 | 440 |
| 13 | 10.5.1 | Information back-up | Back-up copies of information and software should be taken and tested regularly in accordance with the agreed backup policy. | € 750,00 | 228 |
| 14 | 10.6.1 | Network controls | Networks should be adequately managed and controlled, in order to be protected from threats, and to maintain security for the systems and applications using the network, including information in transit. | € 500,00 | 460 |
| 15 | 10.6.2 | Security of network services | Security features, service levels, and management requirements of all network services should be identified and included in any network services agreement, whether these services are provided inhouse or outsourced. | € 600,00 | 500 |
| 16 | 10.8.1 | Information exchange policies and procedures | Formal exchange policies, procedures, and controls should be in place to protect the exchange of information through the use of all types of communication facilities. | € 400,00 | 260 |
| 17 | 10.8.4 | Electronic messaging | Information involved in electronic messaging should be appropriately protected. | € 200,00 | 520 |
| 18 | 10.8.5 | Business information systems | Policies and procedures should be developed and implemented to protect information associated with the interconnection of business information systems. | € 400,00 | 270 |
| 19 | 10.9.1 | Electronic commerce | Information involved in electronic commerce passing over public networks should be protected from fraudulent activity, contract dispute, and unauthorized disclosure and modification. | ? | ? |
| 20 | 10.10.1 | Audit logging | Audit logs recording user activities, exceptions, and information security events should be produced and kept for an agreed period to assist in future investigations and access control monitoring. | € 200,00 | 515 |
| 21 | 10.10.2 | Monitoring system use | Procedures for monitoring use of information processing facilities should be established and the results of the monitoring activities reviewed regularly. | € 200,00 | 635 |
| 22 | 10.10.3 | Protection of log information | Logging facilities and log information should be protected against tampering and unauthorized access. | € 600,00 | 675 |
| 23 | 10.10.4 | Administrator and operator logs | System administrator and system operator activities should be logged. | € 200,00 | 250 |
| 24 | 11.1.1 | Access control policy | An access control policy should be established, documented, and reviewed based on business and security requirements for access. | € 400,00 | 425 |
| 25 | 11.2.1 | User registration | There should be a formal user registration and de-registration procedure in place for granting and revoking access to all information systems and services. | € 200,00 | 80 |
| 26 | 11.2.2 | Privilege management | The allocation and use of privileges should be restricted and controlled. | € 400,00 | 490 |
| 27 | 11.2.3 | User password management | The allocation of passwords should be controlled through a formal management process. | € 700,00 | 225 |
| 28 | 11.2.4 | Review of user access rights | Management should review users access rights at regular intervals using a formal process. | € 400,00 | 475 |
| 29 | 11.3.1 | Password use | Users should be required to follow good security practices in the selection and use of passwords. | € 400,00 | 395 |
| 30 | 11.3.2 | Unattended user equipment | Users should ensure that unattended equipment has appropriate protection. | € 400,00 | 585 |
| 31 | 11.4.1 | Policy on use of network services | Users should only be provided with access to the services that they have been specifically authorized to use. | € 400,00 | 305 |
| 32 | 11.4.6 | Network connection control | For shared networks, especially those extending across the organizations boundaries, the capability of users to connect to the network should be restricted, in line with the access control policy and requirements of the business applications. | € 400,00 | 460 |
| 33 | 11.5.1 | Secure log-on procedures | Access to operating systems should be controlled by a secure log-on procedure. | € 500,00 | 230 |
| 34 | 11.5.2 | User identification and authentication | All users should have a unique identifier (user ID) for their personal use only, and a suitable authentication technique should be chosen to substantiate the claimed identity of a user. | € 700,00 | 230 |
| 35 | 11.5.3 | Password management system | Systems for managing passwords should be interactive and should ensure quality passwords. | € 700,00 | 155 |
| 36 | 11.5.4 | Use of system utilities | The use of utility programs that might be capable of overriding system and application controls should be restricted and tightly controlled. | € 400,00 | 400 |
| 37 | 11.5.5 | Session time-out | Inactive sessions should shut down after a defined period of inactivity. | € 200,00 | 160 |
| 38 | 11.5.6 | Limitation of connection time | Restrictions on connection times should be used to provide additional security for high-risk applications. | € 200,00 | 220 |
| 39 | 11.6.1 | Information access restriction | Access to information and application system functions by users and support personnel should be restricted in accordance with the defined access control policy. | € 500,00 | 375 |
| 40 | 12.3.1 | Policy on the use of cryptographic controls | A policy on the use of cryptographic controls for protection of information should be developed and implemented. | € 250,00 | 260 |
| 41 | 12.4.1 | Control of operational software | There should be procedures in place to control the installation of software on operational systems. | € 500,00 | 235 |
| 42 | 12.3.2 | Key management | Key management should be in place to support the organizations use of cryptographic techniques | € 200,00 | 355 |
| 43 | 12.4.2 | Protection of system test data | Test data should be selected carefully, and protected and controlled. | ? | ? |
| 44 | 12.5.4 | Information leakage | Test data should be selected carefully, and protected and controlled. | € 700,00 | 395 |
| 45 | 13.1.1 | Reporting information security events | Information security events should be reported through appropriate management channels as quickly as possible. | € 300,00 | 615 |
| 46 | 14.1.1 | Including information security in the business continuity management process | A managed process should be developed and maintained for business continuity throughout the organization that addresses the information security requirements needed for the organizations business continuity. | € 500,00 | 53 |
| 47 | 15.1.1 | Identification of applicable legislation | All relevant statutory, regulatory, and contractual requirements and the organizations approach to meet these requirements should be explicitly defined, documented, and kept up to date for each information system and the organization. | €1000,00 | 255 |
| 48 | 15.2.1 | Compliance with security policies and standards | Managers should ensure that all security procedures within their area of responsibility are carried out correctly to achieve compliance with security policies and standards. | € 400,00 | 260 |
| 49 | 15.2.2 | Technical compliance checking | Information systems should be regularly checked for compliance with security implementation standards. | € 600,00 | 246 |
| 50 | 15.3.1 | Information systems audit controls | Audit requirements and activities involving checks on operational systems should be carefully planned and agreed to minimize the risk of disruptions to business processes. | € 500,00 | 70 |
| 51 | 15.3.2 | Protection of information systems audit tools | Access to information systems audit tools should be protected to prevent any possible misuse or compromise. | € 500,00 | 220 |
Appendix I: Inventory of information Systems[15]
| System | Owner | ||||
|---|---|---|---|---|---|
| OSIRIS | Examination Board | ||||
| BlackBoard | Computer & Communicatiezaken (C&CZ) | ||||
| Share | Computer & Communicatiezaken (C&CZ) | ||||
| Persoonlijk rooster | Computer & Communicatiezaken (C&CZ) | ||||
| Portal | Computer & Communicatiezaken (C&CZ) | ||||
| RU | Computer & Communicatiezaken (C&CZ) | ||||
| Studiegids | Examination Board | ||||
| Zoeksysteem UB | Studielandschap | ||||
| Wiki lab | Aangewezen persoon. Op dit moment Hanno Wupper. | ||||
| RUhosting | Computer & Communicatiezaken (C&CZ) | ||||
| Wireless | Computer & Communicatiezaken (C&CZ) | ||||
| VPN | Computer & Communicatiezaken (C&CZ) | ||||
| Surfspot | Computer & Communicatiezaken (C&CZ) | ||||
| Netwerk | Computer & Communicatiezaken (C&CZ) | ||||
Sources
- ↑ http://www.ru.nl/science/
- ↑ http://www.businessdictionary.com/definition/information-security.html
- ↑ http://rominco.net/sidemenu_knowledge_security.html
- ↑ http://www.opensecurityarchitecture.org/cms/definitions/it_security_requirements
- ↑ http://www.information-security-policies-and-standards.com/scope.htm
- ↑ 6,0 6,1 6,2 BSI, BS ISO-IEC 27002 2005, Roles and responsibilities, 31 july 2007 Citefout: Ongeldig label
<ref>; de naam "BS_ISO-IEC_27002_2005" wordt meerdere keren met andere inhoud gedefinieerd. Citefout: Ongeldig label<ref>; de naam "BS_ISO-IEC_27002_2005" wordt meerdere keren met andere inhoud gedefinieerd. - ↑ http://www.privacycommission.be/sites/privacycommission/files/document/richtsnoeren_informatiebeveiliging_0.pdf
- ↑ http://nl.wikipedia.org/wiki/Kwaliteitscirkel_van_Deming
- ↑ 9,0 9,1 http://www.google.nl/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0CDEQFjAA&url=http%3A%2F%2Fwww.ru.nl%2Fpublish%2Fpages%2F578936%2Fjaltena.pdf&ei=fp3MUInDFsiY0QXj0oHQDg&usg=AFQjCNFofdQB126PDC-WFnecqa-a8P2GvA&bvm=bv.1355325884,d.d2k
- ↑ http://www.sans.org/reading_room/whitepapers/iso17799/security-controls-service-management_33558
- ↑ http://www.google.nl/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&ved=0CDEQFjAA&url=http%3A%2F%2Fwww.amsterdam.nl%2Fpublish%2Fpages%2F373750%2Finventarisatie_bri_en_dict_3_juni_2011v10.pdf&ei=zC_PULOLHKTG0QWW2YCAAg&usg=AFQjCNENUH790N1LaIAU2ENHfbnyG4XggA&bvm=bv.1355325884,d.d2k
- ↑ http://www.amersfoort.nl/docs/bis/college/besluiten/2012/week%2023/4116692%20-%20%20Informatiebeveiligingsbeleid%202012-2015.pdf
- ↑ https://www.google.nl/url?sa=t&rct=j&q=&esrc=s&source=web&cd=2&ved=0CEMQFjAB&url=https%3A%2F%2Fwww.ncsc.nl%2Fbinaries%2Fnl%2Fdienstverlening%2Fexpertise-advies%2Fkennisdeling%2Fwhitepapers%2Fwhitepaper-cloudcomputing%2F1%2FNCSC%252BWhitepaperCloudcomputing.pdf&ei=LDDPUI3QAuqc0QXNpYDADw&usg=AFQjCNGB6X9olGofAeuDEeMjrRsrQC42QA&bvm=bv.1355325884,d.d2k&cad=rja
- ↑ http://www.cs.ru.nl/~klaus/secorg/Slides/02_IS_IMPL_20v0.51.pdf
- ↑ http://www.radboudnet.nl/personeel/privacybescherming/
Planning
| Wie | Taak | Periode | Deadline | Status (%) | Indien niet af, waarom niet en wat ga je eraan doen om het op te lossen? |
|---|---|---|---|---|---|
| Edwin | Hoofdstuk 1 | 19-11-2012 tot 26-11-2012 | 26-11-2012 | 100% | |
| Edwin | 1.1 | 19-11-2012 tot 26-11-2012 | 26-11-2012 | 100% | |
| Ahmed | 1.2 | 19-11-2012 tot 26-11-2012 | 26-11-2012 | 100% | |
| Ahmed | 1.3 | 19-11-2012 tot 26-11-2012 | 26-11-2012 | 100% | |
| Ahmed | Hoofdstuk 2 | 26-11-2012 tot 03-12-2012 | 3-12-2012 | 100% | |
| Edwin | 3.1 | 26-11-2012 tot 03-12-2012 | 3-12-2012 | 100% | |
| Ahmed | 3.2 | 26-11-2012 tot 10-12-2012 | 10-12-2012 | 100% | |
| Edwin | 3.3 | 26-11-2012 tot 03-12-2012 | 3-12-2012 | 100% | |
| Ahmed & Edwin | Hoofdstuk 4 | 03-12-2012 tot 10-12-2012 | 10-12-2012 | 100% | |
| Ahmed & Edwin | Hoofdstuk 5 | 10-12-2012 tot 17-12-2012 | 17-12-2012 | 100% | |
| Ahmed & Edwin | Appendix | 19-11-2012 tot 17-12-2012 | 17-12-2012 | 100% | |
| Ahmed & Edwin | Afronden en opleveren opdracht | 17-12-2012 | 17-12-2012 | 100% | Het geheel in word ordenen en als PDF opsturen. |